Nearly every business handles some form of sensitive information, from detailed medical records to credit card information. If your business does not have a plan in place to protect whatever type of personal data it collects, it should.
Why You Need A WISP
A written information security plan, commonly abbreviated as a WISP, outlines how a particular company will protect sensitive information. A WISP generally will include guidelines and protocols for both preventing and reacting to any sort of security breach. Implementing a WISP demonstrates a business’s commitment to client confidentiality and data security.
For certain companies, a WISP is not only prudent, but legally required. For example, The Gramm-Leach-Bliley Act requires financial institutions to protect customer data. In response to this law, the Federal Trade Commission issued the Safeguards Rule, which specifies that tax preparation and accounting firms are bound by the law’s requirement, regardless of their size. The Safeguards Rule also specifies that financial institutions must implement a WISP in order to properly comply with the law.
This example applies to Palisades Hudson, but tax preparers are not the only ones instituting WISPs to comply with legal requirements. For example, health care providers often create a WISP as part of their compliance with federal law restricting the release of medical information.
In addition to federal requirements, many states have passed laws about how and when companies must disclose data breaches. Some states also require a WISP or a similar formal plan for data security. You will need to be sure you understand these laws in any state where your company does business. This includes not only the state where your business is located, but any states where your clients or customers reside as well. Depending on the nature of your business, keeping up with diverse state requirements may be beyond the scope of what you can evaluate internally; in that case, it is wise to consult a professional who can give you the information you need to create your plan.
Whether the law requires a WISP for your business or not, a detailed security plan is a good idea, especially if you handle a lot of sensitive client information. Such data may include Social Security numbers; credit card or financial account information; addresses and phone numbers; passport numbers; and a variety of other information clients wouldn’t want to make public. Clients who trust you with such data will want to know that you have thought through how you will protect such information.
Over the past decades, internet threats have become both more sophisticated and broader in scope. While brute force attacks may be top of mind, client data may also be exposed through phishing attempts, an insider accessing information for personal gain, or even by accident (whether your own or a vendor’s). As with offline disasters such as fires or floods, making a detailed plan in advance can help staff members rapidly address potential vulnerabilities or identify workarounds before problems arise.
A detailed WISP offers a variety of benefits:
- WISPs help firms to identify potential vulnerabilities and risks to sensitive data before bad actors can exploit them or they are accidentally exposed.
- Well-made WISPs outline specific security measures that firms will take as proactive defenses against threats to sensitive information.
- WISPs provide clear roadmaps for incident responses. If firms are hit with a security breach, data loss or ransomware attack, a WISP can help to minimize the damage and to quickly restore operations.
- Implementing a WISP can help firms to avoid reputational damage and, for industries where a plan is required, penalties or other legal repercussions. In 2022, a job placement service company in Massachusetts was fined $230,000 when the company suffered a data breach without a plan to protect personal information already in place.
A WISP is not a cure-all. Even so, a thorough and well-considered plan can help you to avoid certain dangers and can mitigate some of the consequences if a breach occurs.
How To Develop A WISP
Solid WISPs will have many traits in common, but the particulars will depend on a firm’s characteristics and vulnerabilities. It is important to assess your firm’s structure honestly and thoroughly, as there is no one-size-fits-all approach for creating a WISP.
As you develop your WISP, you may want to evaluate the sensitive information you collect. Anything you formerly needed but are not required to keep should be disposed of securely. Going forward, try to avoid collecting any sensitive data that isn’t essential for your business operations. The less sensitive data you collect and store, the less data will be at risk in a breach.
Besides considering the nature of your business and the information it collects, you will want to allow for the complexity of its infrastructure. If your business is particularly large or complex, you may want to consider hiring a compliance company. Compliance professionals will understand how to partner with you to create a WISP that meets any legal requirements and that addresses the many facets of your firm’s operations. You may also seek out legal professionals experienced in this area to review your plan.
If you decide to draft your own WISP, there is still plenty of help available. Whether you are creating a WISP for the first time or you are updating an existing plan, you will find many useful resources online. For tax professionals, a good place to start is the Internal Revenue Service’s website. The IRS provides a guide for tax professionals and accountants that will walk you through the basics of creating a WISP. The guide includes a sample WISP that can serve as a template. In addition, the FTC offers a Data Breach Response guide, which businesses subject to the commission will likely find useful in forming their incident response plans.
Since Palisades Hudson falls under the FTC’s Safeguards Rule, our WISP had to meet certain requirements. Many of these are smart to include, even if your firm is not required to do so by law. Here are a few:
- The plan designates a qualified individual to coordinate the firm’s information security efforts.
- The plan describes how the company planned to identify and evaluate particular risks to client data, including an evaluation of the safeguards that were in place when we developed the WISP.
- The WISP details an updated data safety plan, including future commitments to monitor and update the plan as necessary.
- The plan lays out how the firm will comply with reporting requirements to the FTC in the event of a data breach.
This list is not comprehensive, but it gives you an idea of some of the sections a well-made WISP will include.
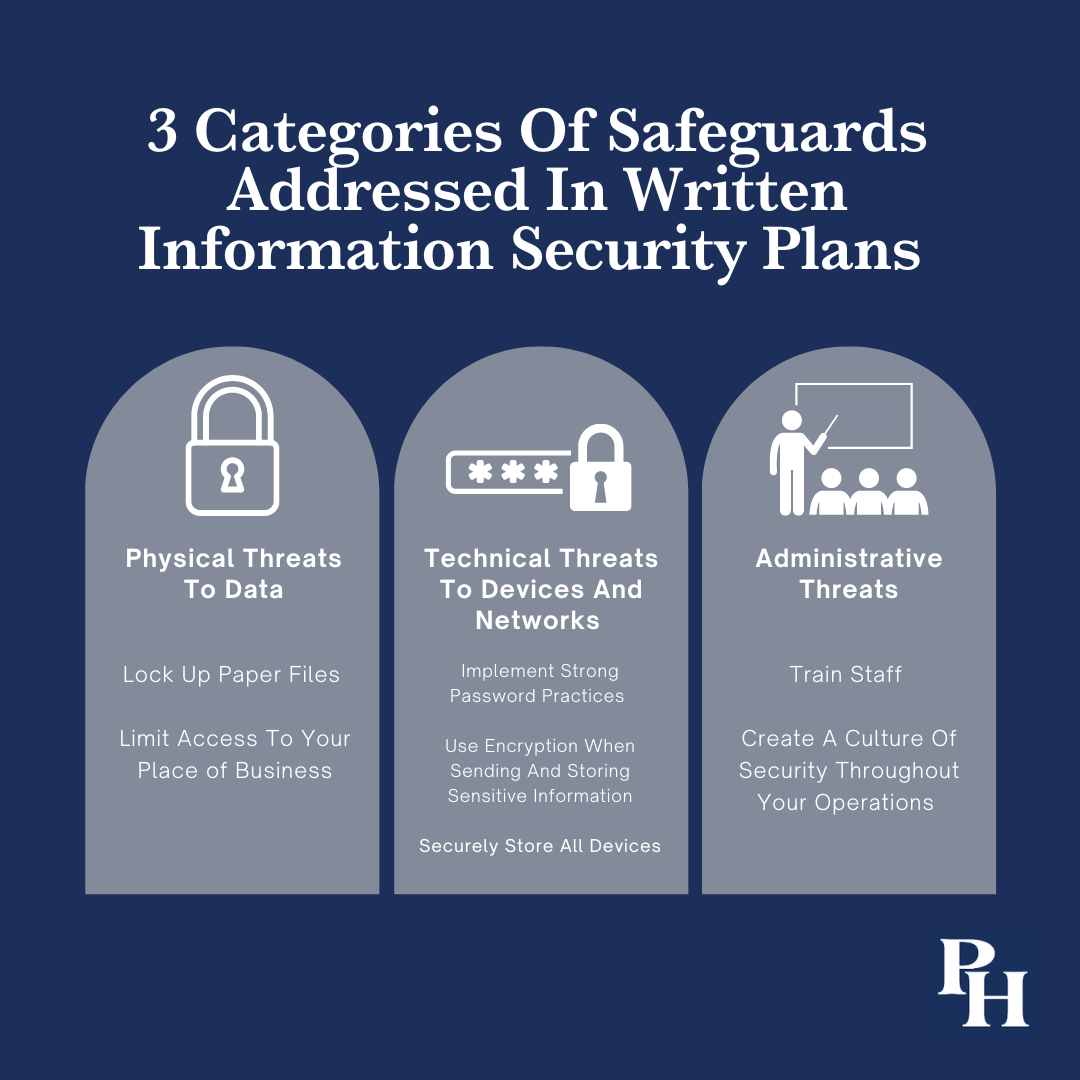
It is likely that your firm’s WISP will address three major categories of safeguards: physical threats to data, technical threats to devices and networks, and administrative threats (for example, phishing attacks aimed at employees). All three areas are important when protecting client data. Protecting against physical threats will involve strategies such as locking up paper files and limiting access to your place of business. Avoiding technical threats will mean implementing strong password practices (including multifactor authentication whenever possible), using encryption when sending and storing sensitive information, and requiring employees to store laptops and mobile devices securely. You will mainly fight administrative threats through training staff and creating a culture of security throughout your operations.
A good WISP should also include a hardware inventory. Catalog any devices where employees access client data, including personal devices when applicable. For example, you may allow employees to check their work emails on personal phones or laptops. If so, you will want to catalog what safeguards you require for such devices.
Depending on the nature of your business, it may also be a good idea to make a list of employees who have access to sensitive client information. This may include outside vendors, if necessary, and former employees or vendors who had access that the business has since terminated. Such a list will demonstrate your attention to security and may make it easier to identify the source of a problem, whether deliberate or accidental.
In addition to laying out your plan to prevent data breaches, your WISP should cover the actions your firm will take if a breach occurs despite your best efforts. The specifics will depend on your company and the nature of the exposed data. At a minimum, you should lay out steps your team will take to stop additional data loss, notify the necessary parties and fix the underlying vulnerability at fault.
Many firms will let their information technology team take the lead in developing a WISP, which makes sense. IT professionals are likely to have a better understanding of the current state of the firm’s data security and common points of vulnerability. That said, it is important to ensure major stakeholders are on board before you implement your WISP. The exact development and review process will depend on your company’s structure, but ensure that decision-makers understand the importance of the WISP and agree with the proposed approach before it takes effect.
Once your company’s WISP is finalized, it is a good idea to create an acknowledgment form for employees and contractors. These demonstrate that you have made your written plan available to staff and create a record of compliance. An acknowledgment of receiving an updated plan annually shows even more diligence, and regular reminders will also help employees keep security policies fresh in their minds. You should provide the WISP to new employees as part of their initial training period.
Creating and implementing a WISP is not enough on its own. A business must also take the time to properly train its employees. Staff members should understand the specific steps the firm will take to secure sensitive data, including any tasks that they are responsible for completing. Whatever the details of a particular company’s WISP, protecting personally identifiable client information is a joint effort that requires all employees to participate in mitigating potential threats and risks.
This article is merely a starting point for developing a WISP of your own. But whether your existing plan needs some updates or you are starting from scratch, don’t delay in creating an up-to-date WISP. As with any disaster preparedness, the best plan is one you make long before the disaster in question arrives.












